The Internet of Things (IoT) has revolutionized our world, connecting countless devices and enabling unprecedented levels of automation and efficiency. From smart homes to industrial applications, IoT devices have become an integral part of our daily lives. However, as the number of connected devices continues to grow exponentially, so do the cybersecurity risks associated with them. IoT security vulnerabilities pose a significant threat to both individuals and organizations, as these devices can be exploited by malicious actors to gain unauthorized access to networks, steal sensitive data, and launch devastating cyberattacks.
According to a recent report by Kaspersky, an alarming 43% of businesses have not fully protected their IoT infrastructure, leaving them vulnerable to potential breaches. Furthermore, Statista forecasts that by 2030, there will be over 29 billion IoT devices worldwide, highlighting the urgent need for robust security measures. As the market for IoT end-user solutions is projected to reach around $1.6 trillion by 2025, it is crucial that manufacturers, organizations, and individuals prioritize IoT device security to mitigate the risks posed by cybersecurity vulnerabilities.
The consequences of neglecting IoT security can be severe, as demonstrated by the infamous Mirai botnet cyberattack in 2016. This attack exploited vulnerabilities in IoT devices to create a massive botnet that disrupted internet service for millions of users and took down significant services and websites, including gaming platforms. The incident underscores the importance of addressing IoT security risks proactively to prevent such large-scale attacks from occurring in the future.
Key Takeaways:
- IoT devices are increasingly prevalent in homes, businesses, and industries, but their rapid growth has led to heightened cybersecurity risks.
- A significant portion of businesses have not fully protected their IoT infrastructure, leaving them vulnerable to potential breaches.
- The projected growth in the number of IoT devices and the market value of IoT solutions emphasizes the urgent need for robust security measures.
- The Mirai botnet cyberattack in 2016 highlighted the severe consequences of neglecting IoT security, as it disrupted internet service for millions of users.
- Manufacturers, organizations, and individuals must prioritize IoT device security to mitigate the risks posed by cybersecurity vulnerabilities.
The Rapid Growth of IoT Devices and Cybersecurity Risks
The Internet of Things (IoT) ecosystem is expanding at an unprecedented pace, with a wide array of devices and applications being developed and deployed across various industries such as healthcare, transportation, fitness, and households. While IoT systems have significantly improved operational efficiency and user experience, their rapid growth has also led to heightened cybersecurity risks.
As the number of IoT devices continues to rise, so do the opportunities for IoT device hacking, IoT malware, IoT botnets, and IoT data breaches. The integration of legacy devices further exacerbates these security threats due to disparities in security measures. Attackers often target health data, making the healthcare industry particularly vulnerable to cybersecurity issues stemming from wearable health monitors.
Similarly, smart vehicles in the transportation sector are increasingly susceptible to security problems as their electronic systems can be exploited by hackers. Fitness enthusiasts using wearable IoT devices to track health metrics must also be cautious about the security of their collected data. Even in the comfort of our homes, smart appliances like thermostats and fridges, while enhancing energy efficiency, introduce potential security risks.
As IoT deployments become more complex and computing power increases, it is crucial for security in the IoT space to keep pace. Encryption during transmission and storage, regular security updates, and the implementation of AI/ML algorithms play vital roles in strengthening IoT cybersecurity.
The advent of 5G technology promises to enhance the speed of IoT networks, but it also brings along heightened security risks, necessitating the development and implementation of more robust security protocols. To address these challenges, higher education programs should incorporate topics such as intrusion detection systems, multi-factor authentication, machine learning for predictive security, and the risks associated with default device settings.
| Region | Regulations and Guidelines |
|---|---|
| United States |
|
| European Union |
|
Governments and regulatory bodies worldwide have recognized the importance of addressing IoT cybersecurity issues. In the United States, the Internet of Things Cybersecurity Improvement Act of 2020 and Executive Order 14028 were enacted to tackle these concerns. The European Union has also taken steps to regulate IoT security through the General Data Protection Regulation (GDPR) and the Cybersecurity Act.
As the IoT landscape continues to evolve, it is essential for manufacturers, users, and organizations to work together in implementing robust security measures, ensuring the protection of sensitive data, and mitigating the risks associated with the rapid growth of IoT devices.
Common Threats to IoT Devices
IoT devices face numerous cybersecurity challenges that can compromise their integrity and the security of the networks they connect to. These threats stem from various factors, including the devices’ inherent limitations, the use of insecure protocols, and the lack of user awareness regarding security best practices. Understanding these common threats is crucial for developing effective strategies to enhance IoT network security and protect sensitive data.
Limited Compute and Hardware Resources
One of the primary challenges in securing IoT devices is their limited computational power and hardware resources. Unlike traditional computing devices, IoT devices often have minimal processing capabilities and storage capacity, leaving little room for implementing robust security measures. This limitation makes it difficult to employ advanced encryption algorithms, intrusion detection systems, and other security mechanisms that are essential for protecting against cyber threats.
Varied Transmission Technologies
IoT devices rely on a wide range of transmission technologies to communicate with each other and with central systems. These technologies include Wi-Fi, Bluetooth, Zigbee, and cellular networks, among others. The diversity of transmission methods makes it challenging to establish a standardized approach to IoT network security. Each technology has its own vulnerabilities and attack vectors, requiring tailored security protocols and measures to mitigate risks.
Vulnerable Components
Many IoT devices incorporate off-the-shelf components and software libraries that may contain known vulnerabilities. Manufacturers often prioritize time-to-market and cost-effectiveness over security, leading to the use of outdated or insecure components. Attackers can exploit these vulnerabilities to gain unauthorized access to devices, intercept data transmissions, or launch attacks on the broader network. The Mirai botnet attack in 2016, which compromised thousands of IoT devices and disrupted major websites, exemplifies the severity of such vulnerabilities.
| Vulnerability | Percentage of IoT Devices Affected |
|---|---|
| Weak Passwords | 80% |
| Insecure Network Services | 60% |
| Insecure Ecosystem Interfaces | 70% |
| Lack of Secure Update Mechanisms | 50% |
Lack of User Security Awareness
User behavior and lack of security awareness also contribute to the vulnerability of IoT devices. Many users fail to change default passwords, regularly update device firmware, or follow basic security practices. This negligence leaves devices open to attacks and compromises the overall security posture of IoT networks. Educating users about the importance of IoT security and providing them with easy-to-follow guidelines can help mitigate these risks.
According to a study by Palo Alto Networks in 2020, 98% of IoT device traffic was unencrypted, exposing personal and confidential data to potential breaches.
Addressing these common threats requires a multi-faceted approach that involves secure device design, regular firmware updates, the implementation of robust encryption protocols, and user education. By prioritizing IoT network security and adopting best practices, we can create a more secure ecosystem that protects devices, data, and users from the ever-evolving landscape of cyber threats.
Impact of IoT Device Vulnerabilities on Users and Networks
The rapid proliferation of IoT devices has brought about a new set of cybersecurity challenges that can have far-reaching consequences for users and networks alike. IoT device vulnerabilities and security threats pose significant risks, as they can be exploited by cybercriminals to gain unauthorized access to sensitive data and compromise the integrity of connected systems.
Lateral Network Movement
One of the most concerning aspects of IoT device vulnerabilities is the potential for lateral network movement. Once an attacker has successfully breached a vulnerable IoT device, they can use it as a foothold to navigate deeper into the network, escalating privileges and spreading malware along the way. This tactic allows cybercriminals to target critical data and systems, causing widespread damage and disruption.
A prime example of lateral network movement through IoT devices occurred in the 2013 Target data breach. Hackers managed to steal login credentials from an HVAC vendor who used IoT sensors, granting them access to Target’s network. This initial breach ultimately led to the exposure of credit card information from millions of transactions, highlighting the severe consequences of inadequately secured IoT devices.
IoT Botnets and Evolving Threats
IoT device vulnerabilities have also given rise to the formation of powerful botnets, which are networks of compromised devices that can be used to launch large-scale cyberattacks. The Mirai botnet attack in 2016 stands as a stark reminder of the destructive potential of these threats. By harnessing a vast network of 145,607 compromised video recorders and IP cameras, the Mirai malware orchestrated a devastating distributed denial of service (DDoS) attack that took down prominent websites and services.
As the number of IoT devices continues to grow, with projections reaching 30.9 billion by 2025 according to Business Insider, the risk of evolving and more sophisticated IoT botnets becomes increasingly alarming. Cybercriminals are constantly adapting their tactics to exploit new vulnerabilities, making it crucial for manufacturers and users to prioritize IoT security measures.
Risks to Household Devices and Corporate Networks
The impact of IoT device vulnerabilities extends beyond the realm of corporate networks, as the technology becomes increasingly prevalent in households. Connected appliances, digital assistants, wearables, and health trackers are just a few examples of the IoT’s permeation into daily life. However, these devices can serve as entry points for attackers to compromise home networks and gain access to sensitive personal information.
Moreover, the rise of remote work and bring-your-own-device (BYOD) policies has blurred the lines between personal and professional technology. If a compromised household IoT device is used to access corporate resources, it can open the door for hackers to infiltrate business networks, leading to data breaches and significant financial losses.
In 2017, researchers discovered that Sonos smart speakers had insecure network services due to simple open ports, exposing sensitive user information to anyone on the internet. This incident underscores the importance of securing household IoT devices to protect both personal and professional data.
The impact of IoT device vulnerabilities on users and networks is a growing concern that demands immediate attention. By addressing these security threats through a combination of manufacturer responsibility, user awareness, and robust cybersecurity practices, we can mitigate the risks posed by the ever-expanding IoT landscape and ensure a safer, more secure digital future.
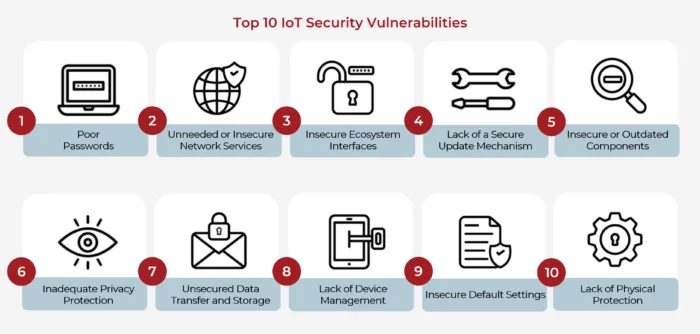
Top IoT Device Vulnerabilities
The rapid growth of IoT devices has led to an increased focus on their security vulnerabilities. With the number of IoT connections in North America alone predicted to reach 5.4 billion by 2025, addressing these vulnerabilities is crucial. IoT device security vulnerabilities can arise from various factors, including weak IoT passwords, insecure IoT networks, and the use of outdated components.
Weak or Hardcoded Passwords
One of the most common IoT device security vulnerabilities is the use of weak or hardcoded passwords. Manufacturers often ship devices with default passwords that are easily guessable, such as “admin” or “1234”. IoT security testing assessments have revealed that a majority of tested devices include guessable passwords and username lists, making them an easy target for attackers.
Insecure Networks and Ecosystem Interfaces
Insecure networks and ecosystem interfaces pose another significant threat to IoT device security. Vulnerabilities in security protocols can lead to unencrypted communication and the use of outdated or vulnerable software in IoT devices. Intruders can exploit poorly secured web, API, or mobile interfaces to gain access to sensitive data within an IoT ecosystem.
| Vulnerability | Percentage of IoT Devices Affected |
|---|---|
| Insufficient processing power | 91% |
| Insecure network services | 78% |
| Weak or hardcoded passwords | 64% |
Lack of Secure Update Mechanisms
IoT devices that lack secure update mechanisms are prone to specific exploits or vulnerabilities due to outdated software or firmware. Without a proper update process, these devices remain exposed to known security risks, allowing attackers to compromise them easily.
Compromised IoT devices may lead to lateral network movement, botnets, unauthorized data access, and DDoS attacks.
Use of Insecure or Outdated Components
Many IoT devices are built using outdated or insecure third-party components, which can be exploited by attackers to compromise device security. The use of open-source code or legacy systems in the IoT ecosystem can introduce vulnerabilities that expand an organization’s attack surface.
To mitigate these IoT device security vulnerabilities, it is essential to use strong, unique passwords, secure network protocols, and regularly update device software and firmware. Segregating IoT devices on separate networks and using antivirus software can also help protect against potential threats.
Cybersecurity Vulnerabilities in IoT Devices: A Growing Concern
With the rapid proliferation of Internet of Things (IoT) devices, IoT cybersecurity risks and IoT security challenges have become increasingly pressing concerns. As the number of active IoT devices is predicted to reach a staggering 20.1 billion by 2025, the potential attack surface for cybercriminals continues to expand at an alarming rate. The Mirai Botnet attack, which caused over 170,000 websites to go offline, serves as a stark reminder of the devastating consequences of inadequate IoT security measures.
Currently, there are approximately 17.08 billion IoT devices in use worldwide, and this number is expected to skyrocket to 41.6 billion by 2025, according to IDC forecasts. While this rapid growth brings numerous benefits and opportunities, it also introduces a myriad of cybersecurity vulnerabilities that must be addressed. Traditional monitoring tools often fall short in securing IoT devices due to their limited visibility and the risk of disruptive scans causing sensitive devices to crash.
Many IoT devices lack essential built-in safeguards, fail to produce logs, and cannot be easily updated or patched. Moreover, they often do not support the installation of endpoint agents, rendering them invisible to conventional security tools. This lack of visibility and control creates significant challenges for organizations striving to maintain a robust security posture in the face of evolving IoT cybersecurity risks.
In the first half of 2024, malware attacks on IoT devices surged by an astonishing 107%, with these devices spending an average of 52.8 hours under attack, as reported in SonicWall’s 2024 Mid-Year Cyber Threat Report.
To effectively combat the growing range of IoT security challenges, a multi-faceted approach is necessary. Some key strategies include:
- Creating a comprehensive device inventory or asset register to account for all known devices in operation
- Referring to IoT security best practice standards and regulations, such as ETSI EN 303 645, for thorough risk assessment
- Changing default credentials on all IoT devices to prevent unauthorized access
- Securing Wi-Fi networks by changing default SSID and password, enabling network encryption, and disabling features like remote management and UPnP
- Implementing network segmentation to separate IoT devices from the main network, minimizing the impact of potential breaches
- Obtaining IoT certifications, such as PSTI statement of compliance, IASME IoT Cyber Scheme, or BSI Kitemark, to validate device security capabilities
Furthermore, empowering the workforce with security awareness training can play a vital role in enhancing IoT cybersecurity. Continuous monitoring for unusual device and user activity, without disrupting organizational operations, is also crucial. Adopting industry best practices, such as the Zero Trust security framework and network segmentation, can further bolster IoT security defenses.
| Industry | IoT Cybersecurity Impact |
|---|---|
| Healthcare | Despite a 15% decrease in vulnerabilities in the first half of 2023, there was a 31% increase in compromised health records, affecting 40 million people (Critical Insight, 2023). |
| Energy | The energy sector ranks as the third most targeted sector for cyber attacks, highlighting its susceptibility to cybersecurity threats (IBM X-Force, 2023). |
As the global base of IoT devices connected to mobile networks is projected to grow by 90% over the next four years, reaching 6.5 billion by 2028 (Juniper Research), the importance of robust IoT cybersecurity measures cannot be overstated. Automated remediation and policy enforcement are essential to limit cyber risk exposure in IoT devices, while end-to-end encryption (E2EE) remains a critical security strategy to protect data privacy and integrity.
Insufficient Privacy Protection and Data Security in IoT Devices
As the number of active IoT devices continues to grow, with projections indicating that it will exceed 25.4 billion by 2030, the need for robust privacy protection and data security measures becomes increasingly critical. IoT devices often collect sensitive personal data, which organizations must securely store and process to comply with various data privacy regulations. Failing to protect this data can lead to significant consequences, including fines, reputational damage, and loss of business.
One of the primary IoT privacy risks stems from the lack of encryption on data transfers between devices and their networks. Without proper encryption, sensitive information becomes vulnerable to cyber-attacks and unauthorized access. Additionally, many IoT devices use outdated software and firmware versions that have not been patched against known exploits, further increasing their susceptibility to security breaches.
Weak, guessable, or hard-coded passwords rank as the top security risk for IoT applications and devices, with approximately five password sets granting access to 10% of all connected IoT devices.
To mitigate these IoT privacy risks and enhance data protection, several measures can be implemented:
- Deploying strong authentication mechanisms, such as multi-factor authentication (MFA)
- Implementing robust encryption protocols for data transmission and storage
- Regularly updating software and firmware to address known vulnerabilities
- Conducting thorough testing during the development phase to identify and fix potential security flaws
The table below highlights some of the key statistics related to IoT privacy risks and data protection:
| Statistic | Value |
|---|---|
| Percentage of device owners who do not change default passwords | 15% |
| Percentage of network-connected endpoints that are IoT devices | 30% |
| Number of active IoT devices as of 2021 | 10+ billion |
| Projected number of active IoT devices by 2030 | 25.4+ billion |
By addressing these IoT privacy risks and implementing robust data protection measures, organizations can ensure the integrity and reliability of their IoT applications while maintaining the trust of their users. As the IoT landscape continues to evolve, it is crucial for manufacturers, users, and organizations to share the responsibility of securing these devices and safeguarding the sensitive data they collect and transmit.
Consequences of Improper IoT Device Management
The rapid proliferation of IoT devices has led to a significant increase in cybersecurity risks, particularly when these devices are not managed properly throughout their lifecycle. Failing to implement robust IoT device management practices can have severe consequences for both individuals and organizations, leaving them vulnerable to cyber attacks and data breaches.
Insecure Default Settings
One of the most common issues with IoT devices is that they often ship with default and hardcoded settings, which are designed to enable simple setup for users. However, these default settings are highly insecure and can be easily exploited by attackers. According to a recent study, a staggering 60% of IoT devices have weak or default passwords, making them an easy target for cybercriminals.
The Ring Home Security Camera breach is a prime example of the dangers posed by insecure default settings. In 2019, hackers were able to gain access to Ring cameras due to weak or default credentials, allowing them to spy on unsuspecting users and even communicate with them through the devices. This incident highlights the importance of changing default passwords and implementing strong authentication measures for IoT devices.
Lack of Physical Hardening
Another major concern for IoT devices is the lack of physical hardening, particularly when these devices are deployed in remote environments. Unlike traditional computing devices that are typically housed in controlled situations, IoT devices are often deployed in the field, making them more susceptible to physical tampering and attacks.
Lack of physical hardening is a major concern for IoT devices, particularly due to remote deployment, exposing vulnerabilities and facilitating potential attacks.
The nature of IoT device deployment makes them easier for attackers to target, disrupt, manipulate, or sabotage. In sectors like healthcare, where IoT devices are used to monitor patient vital signs and administer treatments, the lack of physical hardening can have life-threatening consequences if these devices are compromised.
| IoT Device Management Issue | Potential Consequence |
|---|---|
| Insecure default settings | Unauthorized access to devices and networks |
| Lack of physical hardening | Physical tampering and sabotage of devices |
| Insufficient device visibility | Inability to monitor and respond to threats |
| Unpatched vulnerabilities | Increased risk of malware infections and data breaches |
To mitigate the risks associated with improper IoT device management, organizations must implement comprehensive security strategies that include:
- Regular device discovery and inventory management
- Continuous monitoring and risk assessment
- Timely patching and updates for identified vulnerabilities
- Enforcement of strong authentication and access controls
- Employee training on IoT device security best practices
By adopting a proactive approach to IoT device management and investing in advanced security solutions, organizations can effectively protect their networks and data from the growing threats posed by insecure IoT settings and improper device management practices.
Shared Responsibility in Securing IoT Devices
Ensuring the security of IoT devices requires a collaborative effort from manufacturers, users, and organizations. By adopting IoT security best practices and implementing effective IoT device security measures, stakeholders can significantly reduce the risk of cybersecurity incidents. This shared responsibility model is crucial for maintaining the integrity and safety of IoT ecosystems.
Role of Manufacturers
IoT device manufacturers play a critical role in establishing a strong foundation for device security. They must prioritize security throughout the product lifecycle, from design and development to deployment and support. Key responsibilities of manufacturers include:
- Addressing known vulnerabilities and releasing timely patches
- Conducting thorough security testing to identify and mitigate potential risks
- Providing clear end-of-support dates and communicating them to users
- Implementing secure boot processes and signed firmware to prevent unauthorized code execution
- Offering comprehensive security solutions, such as the Digi TrustFence® platform, which includes features like secure boot, encrypted storage, and secure updates
User Responsibilities
End-users also have a significant role in maintaining the security of their IoT devices. They must stay informed about potential security risks and take proactive measures to protect their devices and networks. User responsibilities include:
- Changing default passwords and using strong, unique passwords for each device
- Regularly updating device firmware and software to the latest versions
- Securing connected devices, such as laptops, smartphones, and routers, to prevent unauthorized access
- Being cautious when granting permissions to IoT apps and services
- Monitoring device activity for unusual behavior and promptly reporting any suspicious activity
Organizational Measures
Organizations deploying IoT devices must implement robust security measures to protect their networks and data. They should assess their existing security frameworks to identify potential weaknesses and take steps to address them. Key organizational measures include:
- Implementing strong authentication and access control mechanisms
- Encrypting sensitive data both at rest and in transit
- Segmenting IoT devices from other network resources to limit the impact of potential breaches
- Regularly monitoring and auditing IoT device activity for anomalies
- Developing and enforcing comprehensive IoT security policies and procedures
The table below highlights the different security requirements for various industries:
| Industry | Security Requirements |
|---|---|
| Retail and Financial Institutions | High level of security for processing transactions |
| Healthcare Organizations | Very high level of security for handling sensitive personal information |
| Other Industries | Varying levels of security based on specific use cases and cost considerations |
By embracing a shared responsibility model and implementing IoT security best practices, manufacturers, users, and organizations can work together to create a more secure and trustworthy IoT ecosystem. This collaborative approach is essential for mitigating the risks posed by cybersecurity vulnerabilities and ensuring the long-term success of IoT technologies.
Solutions for Mitigating IoT Device Vulnerabilities
As the number of IoT devices continues to grow, with over 10 billion currently in use, it is crucial to implement effective IoT security solutions to mitigate vulnerabilities. Comprehensive protections, such as those offered by Trend Micro, provide robust safeguards against threats to IoT devices. These solutions include features that detect malware at the endpoint level, ensuring that connected devices remain secure.
One effective approach to IoT vulnerability mitigation is the use of security software like Trend Micro Home Network Security solutions. These solutions monitor internet traffic between the router and all connected devices, identifying and blocking potential threats. By employing advanced techniques such as AI and machine learning, these security solutions can detect attacks based on historical data. Various ML algorithms, including Linear Discriminant Analysis (LDA) and Random Forest, are utilized for accurate attack identification and classification.
For enterprises, network appliances like the Trend Micro Deep Discovery Inspector offer an additional layer of protection. This appliance monitors all ports and network protocols, detecting advanced threats and safeguarding organizations from targeted attacks. By implementing such solutions, businesses can significantly reduce the risk of IoT-related security breaches, which have surged by 100% in the first half of 2021 alone.
“IoT security is a shared responsibility. Manufacturers must prioritize security in the design and development of IoT devices, while users and organizations must adopt best practices to protect their connected ecosystems.”
To effectively mitigate IoT vulnerabilities, a multi-faceted approach is necessary. This includes:
- Regularly updating IoT devices with the latest security patches and firmware
- Implementing strong, unique passwords for all IoT devices and accounts
- Segmenting IoT devices on separate networks to limit the potential impact of a breach
- Conducting regular security audits and assessments to identify and address vulnerabilities
- Educating users on best practices for IoT device security, such as avoiding public Wi-Fi networks and disabling unused features
| IoT Security Solution | Key Features | Benefits |
|---|---|---|
| Trend Micro Home Network Security | Monitors traffic between router and connected devices; detects and blocks threats | Protects home IoT devices from malware and targeted attacks |
| Trend Micro Deep Discovery Inspector | Monitors all ports and network protocols; identifies advanced threats | Safeguards enterprises from sophisticated IoT-related attacks and breaches |
| AI and Machine Learning Algorithms | Utilizes historical data to detect attacks; employs LDA and Random Forest for classification | Enhances IoT security by accurately identifying and classifying threats |
By implementing comprehensive IoT security solutions and adopting best practices for device management, users and organizations can significantly reduce the risk of falling victim to the growing threat of IoT-related cyberattacks. As the IoT landscape continues to evolve, it is essential to remain vigilant and proactive in addressing vulnerabilities to ensure the security and integrity of connected devices and networks.
Conclusion
The rapid proliferation of IoT devices has brought unprecedented convenience and efficiency to various industries, but it has also exposed significant cybersecurity vulnerabilities. From weak passwords and outdated firmware to insecure networks and lack of encryption, IoT devices face a wide range of threats that can be exploited by attackers. The potential consequences of these vulnerabilities are far-reaching, including unauthorized access, data theft, and the creation of large-scale botnets.
Securing IoT devices is a shared responsibility among manufacturers, users, and organizations. Manufacturers must prioritize security in the design and development of IoT devices, implementing strong authentication methods, timely patches, and secure update mechanisms. Users play a crucial role in protecting their devices by using strong, unique passwords and staying informed about potential risks. Organizations must adopt a multi-layered defense approach, including network segmentation, data encryption, and regular vulnerability assessments. Compliance with IoT security standards and regulations is also essential.
As the IoT landscape continues to expand, it is crucial to recognize the importance of IoT security. Collaboration between stakeholders, ongoing innovation in security solutions, and increased awareness are key to mitigating the risks posed by IoT device vulnerabilities. By prioritizing security and adopting best practices, we can harness the full potential of IoT devices while protecting against the growing threats in the connected world.