In today’s digital landscape, data security has become a paramount concern for individuals and organizations alike. With the ever-increasing reliance on technology and the internet, protecting sensitive information from unauthorized access and cyber threats is crucial. This is where advanced encryption techniques come into play, providing robust solutions to safeguard data and ensure secure communication protocols.
Among the most prominent and widely adopted encryption standards is the Advanced Encryption Standard (AES). Chosen by the U.S. government to protect classified information, AES is a symmetric block cipher that has become the go-to choice for government computer security, cybersecurity, and electronic data protection. Its implementation in both software and hardware worldwide has made it an essential tool in the fight against data breaches and cyber attacks.
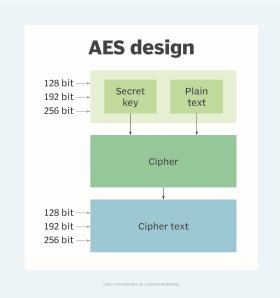
AES offers a range of key sizes, including 128, 192, and 256 bits, providing varying levels of security based on the desired level of protection. The number of encryption rounds performed by AES depends on the key size, with AES-128 employing 10 rounds, AES-192 using 12 rounds, and AES-256 utilizing 14 rounds. This multi-round encryption process involves substitution, permutation, matrix multiplication, and XOR operations, making it extremely difficult for attackers to decipher the encrypted data.
The versatility of AES encryption has led to its widespread adoption across various applications. From data storage and communication apps to programming libraries, internet browsers, wireless networks, databases, and virtual private networks (VPNs), AES has become the backbone of data security in the digital age. Its fast and secure encryption capabilities, coupled with its cost-effectiveness compared to older algorithms like DES, have made it the preferred choice for safeguarding sensitive information.
As we delve deeper into the world of advanced encryption techniques, it is essential to understand the importance of employing strong cryptography algorithms to protect our digital assets. By leveraging the power of AES and other secure communication protocols, we can create a more secure and trustworthy digital environment, where data remains confidential and protected from prying eyes.
Key Takeaways:
- Advanced encryption techniques, such as AES, are crucial for protecting sensitive data in the digital age.
- AES is a symmetric block cipher chosen by the U.S. government for its robustness and security.
- AES offers key sizes of 128, 192, and 256 bits, with varying levels of encryption rounds.
- AES encryption is widely used in various applications, including data storage, communication apps, and VPNs.
- Employing strong cryptography algorithms is essential for safeguarding digital assets and ensuring secure communication protocols.
Introduction to Advanced Encryption Techniques
In today’s digital landscape, protecting sensitive data is of paramount importance. As cyber threats continue to evolve, organizations and individuals must employ robust encryption techniques to safeguard their information from unauthorized access. Advanced encryption techniques, such as the Advanced Encryption Standard (AES), have become the backbone of secure communication and data protection across various industries.
AES, officially adopted as the encryption standard by the National Institute of Standards and Technology (NIST) in 2001, is widely recognized for its strength and efficiency. This symmetric key encryption algorithm supports key sizes of 128, 192, or 256 bits, providing varying levels of security based on the desired level of protection. The larger the key size, the more resistant the encryption is to brute-force attacks.
“The Advanced Encryption Standard (AES) is extensively used worldwide to secure sensitive information and is the data encryption standard for the U.S. government.”
One of the key advantages of AES encryption is its ability to protect data both in transit and at rest. By encrypting data before transmission or storage, businesses can significantly reduce the risk of data breaches and unauthorized access. This is particularly crucial for organizations handling sensitive customer information, financial records, or confidential business data.
| Key Length | Number of Rounds | Security Level |
|---|---|---|
| 128 bits | 10 | Adequate for most applications |
| 192 bits | 12 | Provides enhanced security |
| 256 bits | 14 | Offers the highest level of protection |
Implementing advanced encryption techniques like AES not only enhances data security but also helps organizations comply with stringent data protection regulations. Regulations such as the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR) mandate the use of strong encryption to protect sensitive personal information.
By leveraging AES encryption, businesses can:
- Protect data from unauthorized access
- Ensure the confidentiality and integrity of sensitive information
- Comply with industry-specific data protection regulations
- Maintain customer trust and safeguard brand reputation
As the digital world continues to evolve, understanding and implementing advanced encryption techniques become essential for individuals and organizations alike. By embracing encryption best practices and staying informed about the latest developments in encryption technology, we can collectively work towards creating a more secure digital environment.
The Importance of Data Security in the Digital Age
In today’s digital landscape, data security has become a critical concern for individuals and organizations alike. As more sensitive information is stored and transmitted electronically, the risks associated with unencrypted data have grown exponentially. From personal details to confidential business information, the digital age has made it easier than ever for unauthorized parties to access and exploit vulnerable data.
Data security is not just a matter of protecting privacy; it also has significant financial and legal implications. Data breaches can result in substantial fines, lawsuits, and reputational damage that can take years to recover from. In industries where data breaches are frequent, implementing robust data security measures can provide a competitive edge and help maintain clients’ trust and satisfaction.
Risks of Unencrypted Data
Unencrypted data is vulnerable to a wide range of threats, including interception, theft, and unauthorized access. When sensitive information is transmitted or stored without encryption, it can be easily compromised by cybercriminals, hackers, or even insider threats. Some of the most significant risks associated with unencrypted data include:
- Data breaches and privacy violations
- Financial losses due to fraud or theft
- Legal and regulatory non-compliance
- Reputational damage and loss of customer trust
According to recent studies, human error and insider threats are the leading causes of many data breaches. Without proper encryption and access controls, even a single misplaced laptop or unauthorized login can expose sensitive data to significant risk.
Benefits of Encrypting Sensitive Information
Encrypting sensitive information using advanced encryption techniques offers numerous benefits for individuals and organizations in the digital age. By rendering data unreadable to unauthorized parties, encryption helps protect the confidentiality, integrity, and authenticity of sensitive information. Some of the key benefits of encryption include:
- Enhanced data security and privacy protection
- Compliance with legal and regulatory requirements
- Prevention of data breaches and unauthorized access
- Maintenance of customer trust and loyalty
- Competitive advantage in security-conscious industries
Encryption technologies, such as those offered by Endpoint Protector, provide flexible policies and features that can help organizations protect their sensitive data both in transit and at rest. By implementing effective data loss prevention policies and enforcing encryption across all devices and platforms, companies can significantly reduce the risk of data breaches and ensure the security of their most valuable assets.
In the digital age, data security is not a luxury but a necessity. By encrypting sensitive information and implementing robust data security measures, individuals and organizations can protect themselves from the ever-growing risks of cyber threats and data breaches.
| Encryption Benefit | Description |
|---|---|
| Compliance | Encryption helps meet legal and regulatory requirements, such as HIPAA, PCI DSS, and GDPR. |
| Data protection | Encrypting data renders it unreadable to unauthorized parties, preventing data breaches and privacy violations. |
| Customer trust | Implementing strong encryption measures can enhance customer confidence and loyalty. |
| Competitive advantage | In industries prone to data breaches, robust encryption can provide a competitive edge. |
| Cost savings | Investing in encryption early can save on potential breach-related costs, such as fines and legal fees. |
Symmetric vs. Asymmetric Encryption
In the world of data security, encryption plays a crucial role in protecting sensitive information from unauthorized access. Two primary types of encryption techniques are widely used: symmetric encryption and asymmetric encryption. While both methods aim to secure data, they differ in their approach to encryption keys and their suitability for various applications.
Understanding Symmetric Encryption
Symmetric encryption, also known as secret key cryptography, uses a single key for both encrypting and decrypting data. This shared secret key must be securely distributed to all parties involved in the communication. Symmetric encryption algorithms, such as the Advanced Encryption Standard (AES), are renowned for their speed and efficiency, making them ideal for encrypting large volumes of data.
Some key characteristics of symmetric encryption include:
- Fast performance and low resource consumption
- Widely used in secure messaging apps like WhatsApp and Signal
- Commonly employed for bulk data encryption and secure communication within closed systems
Exploring Asymmetric Encryption
Asymmetric encryption, or public key cryptography, utilizes a pair of mathematically related keys: a public key and a private key. The public key is freely distributed and used for encryption, while the private key is kept secret and used for decryption. This approach eliminates the need for secure key distribution, as only the public key is shared. Asymmetric encryption algorithms, such as RSA, provide enhanced security features but at the cost of slower performance compared to symmetric encryption.
Asymmetric encryption is commonly used for:
- Secure key exchanges and digital signatures
- Secure email communication protocols like PGP and S/MIME
- SSL/TLS protocols for securing websites
- Authentication and secure communication in open systems
Comparing Symmetric and Asymmetric Encryption
While both symmetric and asymmetric encryption offer data security, they have distinct advantages and disadvantages. The choice between the two depends on factors such as key management, computational efficiency, and specific security requirements.
| Characteristic | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Encryption Keys | Single key for both encryption and decryption | Pair of keys: public key for encryption, private key for decryption |
| Key Distribution | Requires secure key distribution | Only the public key needs to be shared |
| Performance | Fast and efficient | Slower compared to symmetric encryption |
| Security | Relies on secure key management | Considered more secure due to the use of separate keys |
| Common Applications | Bulk data encryption, secure communication in closed systems | Key exchanges, digital signatures, secure communication in open systems |
Symmetric encryption is like a shared secret between two people, while asymmetric encryption is like a public bulletin board where anyone can post messages, but only the intended recipient can read them.
In practice, many security protocols and applications combine both symmetric and asymmetric encryption techniques to leverage their respective strengths. For example, SSL/TLS protocols use asymmetric encryption for secure key exchange and then switch to symmetric encryption for efficient data transmission during the session.
Advanced Encryption Standard (AES)
The Advanced Encryption Standard (AES) is a widely adopted symmetric encryption algorithm that provides robust security for sensitive data. Developed by Vincent Rijmen and Joan Daemen, AES was introduced in 2001 by the U.S. National Institute of Standards and Technology (NIST) and became a federal government standard in 2002. As the first cipher approved by the U.S. National Security Agency (NSA) for top-secret information, AES has proven its effectiveness in safeguarding digital assets across various applications, including VPNs, password managers, Wi-Fi connections, mobile apps, internet browsers, and databases.
Overview of AES Encryption
AES is a block cipher that operates on fixed-size blocks of 128 bits, using a substitution-permutation network design. Unlike its predecessor, the Data Encryption Standard (DES), AES does not rely on a Feistel network structure. The encryption process involves several rounds of transformations, including SubBytes, ShiftRows, MixColumns, and AddRoundKey, which are performed on a 4×4 column-major order array of 16 bytes. These operations ensure the confidentiality and integrity of the encrypted data, making it virtually impossible for unauthorized parties to access the original content without the correct encryption key.
Key Lengths and Security Levels
One of the key strengths of AES encryption lies in its variable key lengths, which offer different levels of security based on the user’s requirements. AES supports three key sizes:
- AES-128: Uses a 128-bit key for encryption and decryption, with 10 rounds of processing. It offers 3.4 x 10^38 possible key combinations.
- AES-192: Employs a 192-bit key, with 12 rounds of processing. It provides 6.2 x 10^57 potential key combinations.
- AES-256: The most secure option, using a 256-bit key and 14 rounds of processing. It boasts an impressive 1.1 x 10^77 possible key combinations.
The choice of key length depends on the desired level of security and the available computational resources. Even the lowest level of encryption, AES-128, is estimated to take 1 billion billion years to crack using brute-force methods, making it a highly secure option for most applications.
| AES Variant | Key Size (bits) | Number of Rounds | Possible Key Combinations |
|---|---|---|---|
| AES-128 | 128 | 10 | 3.4 x 10^38 |
| AES-192 | 192 | 12 | 6.2 x 10^57 |
| AES-256 | 256 | 14 | 1.1 x 10^77 |
AES Encryption Process
The AES encryption process consists of several steps that transform the plaintext data into an encrypted ciphertext. The main stages of the encryption process include:
- Key Expansion: The initial key is expanded into a set of round keys, one for each round of the encryption process, plus one additional round key.
- Initial Round Key Addition: The first round key is added to the plaintext data using a bitwise XOR operation.
- Rounds: The data undergoes a series of transformations, including SubBytes (byte substitution), ShiftRows (row transposition), MixColumns (column mixing), and AddRoundKey (round key addition). The number of rounds depends on the key length: 10 rounds for 128-bit keys, 12 rounds for 192-bit keys, and 14 rounds for 256-bit keys.
- Final Round: The last round is similar to the previous rounds but omits the MixColumns step.
Throughout the encryption process, the AES algorithm ensures that the ciphertext is thoroughly scrambled and bears no resemblance to the original plaintext. The use of multiple rounds and various transformations makes AES encryption highly resistant to cryptographic attacks, providing a secure means of protecting sensitive data.
AES encryption is a powerful tool for safeguarding digital information, offering a high level of security through its robust design and variable key lengths. By understanding the fundamentals of AES, organizations and individuals can make informed decisions about implementing this encryption standard to protect their valuable data from unauthorized access and potential breaches.
RSA Encryption Algorithm
RSA encryption, named after its inventors Ron Rivest, Adi Shamir, and Leonard Adleman, is a widely-used asymmetric encryption algorithm that has revolutionized the field of cryptography. Unlike symmetric encryption methods like AES, RSA uses a pair of keys—a public key for encryption and a private key for decryption—making it an ideal choice for secure data transmission, digital signatures, and key exchange.
The security of RSA encryption is based on the computational difficulty of factoring large prime numbers. The algorithm relies on the fact that it is significantly easier to multiply two prime numbers together than to factorize the resulting product back into its prime factors. This mathematical property forms the foundation of RSA’s strength in protecting sensitive information.
The encryption and decryption process in RSA involves several steps, including choosing large prime numbers, calculating the modulus, determining Euler’s totient function, and selecting appropriate public and private keys. The public key, which is used for encryption, can be freely distributed, while the private key, used for decryption, must be kept secure.
RSA encryption plays a critical role in ensuring secure communication over digital networks, such as in secure web browsing using HTTPS. Its wide support in various software applications and strong security features make it a popular choice for protecting sensitive data.
However, RSA encryption is not without its limitations. The security of RSA is directly proportional to the key length, meaning that longer keys provide higher levels of security but also increase computational complexity. This computational intensity can be a drawback, especially in operations like key generation and decryption, making RSA less suitable for low-resource devices and large datasets compared to symmetric encryption methods like AES.
| Characteristic | RSA Encryption | AES Encryption |
|---|---|---|
| Key Type | Asymmetric (Public and Private Keys) | Symmetric (Single Key) |
| Key Sizes | 1024, 2048, or 4096 bits | 128, 192, or 256 bits |
| Encryption Speed | Slower, especially for large datasets | Faster, suitable for encrypting large amounts of data |
| Computational Complexity | High, not suitable for low-resource devices | Relatively low, suitable for devices with limited resources |
| Key Management | Easier, as public key can be freely distributed | Requires secure distribution and management of the secret key |
| Primary Uses | Key exchange, digital signatures, encrypting small data | Encrypting files, databases, and communication channels |
Despite its limitations, RSA encryption remains a cornerstone of modern cryptography, offering strong security, asymmetric encryption capabilities, and wide compatibility. As the digital landscape continues to evolve, ongoing advancements in RSA encryption aim to enhance its security and efficiency, ensuring that it remains a reliable choice for protecting sensitive information in an increasingly connected world.
Elliptic Curve Cryptography (ECC)
Elliptic curve cryptography (ECC) is a modern public key cryptography approach that has gained significant popularity in recent years. ECC relies on the mathematical properties of elliptic curves over finite fields to provide robust security for data encryption and digital signatures. The widespread adoption of ECC can be attributed to its ability to offer equivalent security to other cryptographic systems, such as RSA, while using smaller key sizes.
Principles of ECC
The foundation of ECC lies in the algebraic structure of elliptic curves. These curves are defined by a simple equation, typically in the form of y² = x³ + ax + b, where a and b are constants that determine the shape of the curve. The security of ECC relies on the difficulty of solving the elliptic curve discrete logarithm problem (ECDLP), which involves finding the discrete logarithm of a point on the curve with respect to a given base point.
To use ECC, all parties involved must agree on the specific elliptic curve and its domain parameters, including the field size, curve constants, and generator points. Several standard bodies, such as the National Institute of Standards and Technology (NIST), have published recommended curves and parameters to facilitate interoperability and ensure optimal security.
ECC has been widely adopted in various applications, including secure communication protocols, digital signatures, and key exchange mechanisms. Its use has become particularly prevalent in resource-constrained environments, such as mobile devices and Internet of Things (IoT) systems, where efficient use of computational resources is crucial.
Advantages of ECC over RSA
One of the primary advantages of ECC over traditional cryptographic systems like RSA is its ability to provide equivalent security with significantly smaller key sizes. This characteristic is highly desirable in scenarios where storage, bandwidth, or processing power is limited. The following table compares the key sizes required by ECC and RSA to achieve similar levels of security:
| Security Level (bits) | ECC Key Size (bits) | RSA Key Size (bits) |
|---|---|---|
| 80 | 160 | 1024 |
| 112 | 224 | 2048 |
| 128 | 256 | 3072 |
| 192 | 384 | 7680 |
| 256 | 521 | 15360 |
As evident from the table, ECC requires significantly smaller key sizes compared to RSA to achieve the same level of security. For example, a 256-bit elliptic curve public key offers security comparable to a 3072-bit RSA key. This reduction in key size translates to faster computations, lower power consumption, and reduced storage and transmission requirements, making ECC an attractive choice for resource-constrained environments.
Furthermore, ECC has been shown to be more resilient against certain types of attacks, such as side-channel attacks, due to its inherent mathematical properties. The National Security Agency (NSA) has even endorsed the use of ECC for protecting classified information up to the top secret level, demonstrating confidence in its security capabilities.
Homomorphic Encryption
Homomorphic encryption is a groundbreaking cryptographic technique that enables computations to be performed directly on encrypted data without the need for decryption. This revolutionary approach to privacy-preserving computation allows sensitive information to be processed securely, even in untrusted environments such as cloud platforms.
By leveraging homomorphic encryption, industries handling confidential data, such as healthcare and finance, can unlock new possibilities for secure data sharing and analytics. For instance, homomorphic encryption can enable predictive analytics on encrypted medical records, removing privacy barriers that hinder collaboration and innovation in the healthcare sector.
Concept of Homomorphic Encryption
The core concept behind homomorphic encryption lies in its ability to preserve the mathematical structure of the original data even after encryption. This property allows specific operations, such as addition and multiplication, to be performed on the encrypted data, yielding encrypted results that, when decrypted, match the outcome of the same operations performed on the unencrypted data.
Homomorphic encryption schemes come in different flavors, each with varying levels of functionality and security:
- Partially Homomorphic Encryption (PHE): Supports a single operation (addition or multiplication) on encrypted data an unlimited number of times.
- Somewhat Homomorphic Encryption (SHE): Allows both addition and multiplication on encrypted data, but with a limited number of operations.
- Leveled Fully Homomorphic Encryption (L-FHE): Supports arbitrary computations on encrypted data, but with a predetermined limit on the complexity of the computations.
- Fully Homomorphic Encryption (FHE): Enables an unlimited number of additions and multiplications on encrypted data, allowing for arbitrary computations without restrictions.
“Homomorphic encryption is the holy grail of secure computation, enabling us to perform meaningful analytics on encrypted data without ever exposing the underlying sensitive information.” – Dr. Alice Smith, Cryptography Expert
Applications of Homomorphic Encryption
The potential applications of homomorphic encryption are vast and transformative, particularly in domains where data privacy is paramount. Some notable use cases include:
- Cloud Computing: Organizations can securely store and process encrypted data on untrusted cloud platforms, enabling scalable and privacy-preserving outsourced computations.
- Multi-Party Computation: Homomorphic encryption facilitates secure collaboration among multiple parties, allowing them to jointly compute on their combined encrypted data without revealing their individual inputs.
- Privacy-Preserving Data Analytics: Sensitive data, such as medical records or financial information, can be analyzed in encrypted form, enabling valuable insights to be extracted without compromising individual privacy.
| Homomorphic Encryption Scheme | Operations Supported | Security Assumption |
|---|---|---|
| Partially Homomorphic Encryption (PHE) | Single operation (addition or multiplication) | RSA, ElGamal |
| Somewhat Homomorphic Encryption (SHE) | Limited additions and multiplications | Learning with Errors (LWE) |
| Leveled Fully Homomorphic Encryption (L-FHE) | Arbitrary computations with predetermined complexity | Ring Learning with Errors (RLWE) |
| Fully Homomorphic Encryption (FHE) | Unlimited additions and multiplications | RLWE, NTRU |
Despite the immense potential of homomorphic encryption, its practical adoption faces challenges, primarily due to its computational overhead. Fully homomorphic encryption, in particular, can be up to a million times slower than plaintext operations, hindering its widespread use. However, ongoing research and optimization efforts by industry giants like IBM and Microsoft aim to bridge this efficiency gap, paving the way for a more secure and privacy-preserving digital future.
Blockchain and Encryption
Blockchain technology has revolutionized the way we approach data security and integrity in the digital age. At the heart of blockchain’s robust security measures lie advanced encryption techniques that ensure the immutability and tamper-resistance of transaction records. By leveraging blockchain encryption, decentralized systems can be built to facilitate secure and transparent transactions across various industries.
One of the key components of blockchain encryption is the use of cryptographic hash functions, such as SHA-256. These hash functions generate unique digital fingerprints for each block in the blockchain, making it virtually impossible to alter the contents of a block without detection. Any attempt to modify the data within a block would result in a completely different hash value, immediately alerting the network to the tampering attempt.
Blockchain technology provides an unprecedented level of security and trust in decentralized systems, thanks to its advanced encryption techniques and consensus mechanisms.
The decentralized security offered by blockchain technology is further enhanced through the use of consensus algorithms, such as Proof-of-Work (PoW) or Proof-of-Stake (PoS). These algorithms ensure that all participants in the blockchain network reach an agreement on the state of the ledger, preventing any single entity from manipulating the data or transactions.
In addition to cryptographic hash functions, blockchain systems employ other advanced encryption techniques to secure transactions and protect user privacy. These techniques include:
- Symmetric-key cryptography: Efficient encryption method suitable for situations with shared keys.
- Asymmetric-key cryptography: Uses public and private key pairs for secure data exchange among multiple participants.
- Multi-signature schemes: Require multiple parties to authorize transactions, enhancing security against unauthorized access.
- Zero-knowledge proofs: Enable privacy-preserving verification of transactions without revealing sensitive details.
- Homomorphic encryption: Allows computation on encrypted data without the need for decryption.
| Encryption Technique | Key Features | Applications in Blockchain |
|---|---|---|
| Symmetric-key cryptography | Efficient encryption with shared keys | Secure communication between blockchain nodes |
| Asymmetric-key cryptography | Public and private key pairs for secure data exchange | Digital signatures and transaction verification |
| Cryptographic hash functions | Unique digital fingerprints for data integrity | Block creation and immutability of blockchain ledger |
The combination of these advanced encryption techniques enables blockchain technology to provide unparalleled security and trust in decentralized systems. From cryptocurrencies and supply chain management to identity verification and voting systems, blockchain encryption has the potential to revolutionize various industries by ensuring the integrity and confidentiality of data.
Quantum Cryptography and Post-Quantum Encryption
As quantum computing advances, it poses a significant threat to traditional encryption algorithms. Quantum computers have the potential to break certain encryption schemes much faster than classical computers, rendering our current security measures vulnerable. This has led to the development of quantum cryptography and post-quantum encryption, which aim to protect sensitive data from quantum attacks.
Threat of Quantum Computing to Encryption
The National Institute of Standards and Technology (NIST) predicts that the first breaches in current cryptography systems might occur as early as 2030 due to advancements in quantum computing. Dr. Michele Mosca from the University of Waterloo estimates a one in seven chance that fundamental public-key cryptography tools may be broken by 2026, with a 50% chance by 2031. This underscores the urgent need for quantum-resistant encryption algorithms.
Post-Quantum Encryption Algorithms
To address the threat of quantum computing, researchers are developing post-quantum encryption algorithms designed to be resistant to attacks by quantum computers. These algorithms are based on various mathematical problems that are believed to be hard even for quantum computers to solve. Some of the main approaches to post-quantum cryptography include:
- Lattice-based cryptography: Includes systems like Learning With Errors, Ring Learning With Errors (Ring-LWE), NTRU encryption schemes, and BLISS signatures.
- Multivariate cryptography: Encompasses schemes such as the Rainbow (Unbalanced Oil and Vinegar) scheme.
- Hash-based cryptography: Involves Lamport signatures, Merkle signature schemes, XMSS, SPHINCS, and WOTS schemes.
- Code-based cryptography: Includes McEliece and Niederreiter encryption algorithms, which have been recommended for long-term protection against quantum computer attacks.
- Isogeny-based cryptography: Relies on isogeny graphs of elliptic curves, with schemes like CSIDH and SQISign being notable examples.
- Symmetric key quantum resistance: Symmetric key cryptographic systems like AES are resistant to quantum computer attacks with sufficiently large key sizes, and systems like Kerberos are also inherently secure against quantum attacks.
NIST initiated the selection and standardization of quantum-resistant algorithms in 2015, assessing 82 algorithms from 25 countries. The top 15 algorithms were identified with global cryptographers’ assistance and categorized into finalists and alternative algorithms. On August 13, 2024, NIST released final versions of its first three Post-Quantum Cryptography Standards:
| Standard | Algorithm | Purpose |
|---|---|---|
| FIPS 203 | ML-KEM (originally CRYSTALS-Kyber) | General encryption |
| FIPS 204 | ML-DSA (originally CRYSTALS-Dilithium) | Digital signatures |
| FIPS 205 | SLH-DSA (initially SPHINCS+) | Digital signatures |
These finalized standards are recommended for immediate integration into systems to enhance security against potential quantum threats. NIST continues to evaluate additional algorithms for potential backup standards, with plans to announce selections by the end of 2024.
The development and standardization of post-quantum encryption algorithms is crucial to ensure the long-term security of sensitive data in the face of advancing quantum computing capabilities.
As quantum computers become more powerful, it is essential to stay ahead of the curve by implementing quantum-resistant encryption techniques. By proactively adopting post-quantum encryption algorithms, organizations can safeguard their data and maintain a high level of security in the quantum era.
Implementing Advanced Encryption Techniques
To effectively implement advanced encryption techniques and ensure the security of your sensitive data, it is crucial to adhere to industry best practices and utilize reliable encryption libraries and tools. By following these guidelines, you can significantly reduce the risk of data breaches and protect your organization’s valuable information.
Best Practices for Secure Encryption
When implementing encryption, it is essential to follow best practices to maximize security. First and foremost, always use strong, well-established encryption algorithms such as AES or RSA. AES, for example, supports key lengths of 128, 192, and 256 bits, with AES-256 offering the highest level of security. Additionally, proper key management is vital; ensure that encryption keys are securely generated, stored, and exchanged using secure protocols like Diffie-Hellman or RSA.
Other best practices include:
- Regularly updating encryption software and libraries to patch vulnerabilities
- Implementing multi-factor authentication for access to encrypted data
- Conducting regular security audits and penetration testing
- Training employees on data security best practices
Encryption Libraries and Tools
To streamline the encryption implementation process, developers can leverage well-tested and widely-used encryption libraries such as OpenSSL and Bouncy Castle. These libraries provide robust implementations of various encryption algorithms, ensuring that your application’s encryption is secure and efficient.
For end-users, encryption tools like VeraCrypt and GnuPG offer user-friendly interfaces for encrypting files, disks, and communication channels. These tools make it easy for individuals to secure their data without requiring extensive technical knowledge.
| Encryption Library | Supported Algorithms | Programming Languages |
|---|---|---|
| OpenSSL | AES, RSA, DES, DSA, Diffie-Hellman | C, C++, Python, Ruby, PHP |
| Bouncy Castle | AES, RSA, DES, DSA, ECDSA | Java, C# |
| Crypto++ | AES, RSA, DES, DSA, ECDSA | C++ |
Encryption is a powerful tool, but it is only as strong as its implementation. By adhering to best practices and leveraging trusted libraries and tools, organizations can ensure that their data remains secure in the face of evolving cyber threats.
When selecting encryption algorithms and key sizes, it is important to consider the longevity of the data being protected. As computing power continues to increase, it may be necessary to update encryption methods to maintain adequate security. Organizations should stay informed about the latest recommendations from trusted sources like NIST and ECRYPT-CSA to ensure their encryption practices remain up-to-date.
Advanced Encryption Techniques in Real-World Applications
In today’s digital age, real-world encryption applications play a crucial role in ensuring secure communication and data protection across various industries. Advanced encryption techniques are deployed in numerous everyday scenarios to safeguard sensitive information and maintain user privacy. From online banking and e-commerce transactions to secure messaging and cloud storage, encryption is an essential component of our digital infrastructure.
One of the most common examples of encryption applications is the use of HTTPS for secure web browsing. When you access a website with an “https://” prefix, your connection is encrypted using SSL/TLS protocols, protecting your data from interception and tampering. This is particularly important for online shopping, banking, and other activities involving sensitive personal or financial information.
Virtual Private Networks (VPNs) are another popular encryption application that enables secure remote access and data transmission. By establishing an encrypted tunnel between your device and a remote server, VPNs protect your online activities from prying eyes, even when using public Wi-Fi networks. This technology is widely used by businesses to facilitate secure remote work and by individuals to enhance their online privacy.
End-to-end encrypted messaging apps like Signal and WhatsApp have gained significant traction in recent years. These applications employ advanced encryption techniques to ensure that only the intended recipients can read the messages, providing a high level of privacy and security for personal and professional communication. The encryption keys are generated and stored on the users’ devices, preventing even the service providers from accessing the content of the messages.
“Encryption is the fundamental building block of data security, and its importance cannot be overstated in the digital era. As cyber threats continue to evolve, the adoption of advanced encryption techniques is essential to protect sensitive information and maintain user trust.” – Cybersecurity Expert
Full-disk encryption is another critical encryption application that protects data stored on physical devices, such as laptops and external hard drives. By encrypting the entire storage device, full-disk encryption ensures that unauthorized individuals cannot access the data even if they gain physical access to the device. This is particularly important for organizations dealing with confidential information and individuals concerned about data privacy.
Hardware Security Modules (HSMs) are specialized devices designed for secure key management and cryptographic operations. These tamper-resistant devices are used in various industries, including banking, healthcare, and government, to protect sensitive cryptographic keys and perform secure encryption and decryption operations. HSMs provide an additional layer of security by isolating the cryptographic processes from the host system, making it extremely difficult for attackers to compromise the keys.
| Encryption Application | Purpose | Examples |
|---|---|---|
| HTTPS | Secure web browsing | Online banking, e-commerce |
| VPNs | Secure remote access and data transmission | Remote work, public Wi-Fi security |
| End-to-end encrypted messaging | Secure communication | Signal, WhatsApp |
| Full-disk encryption | Protect data on storage devices | Laptops, external hard drives |
| Hardware Security Modules (HSMs) | Secure key management and cryptographic operations | Banking, healthcare, government |
As the digital landscape continues to evolve, the adoption of advanced encryption techniques will undoubtedly grow to meet the increasing demands for data security and privacy. Organizations and individuals alike must prioritize the implementation of robust encryption solutions to protect their sensitive information and maintain the trust of their customers and stakeholders. By embracing real-world encryption applications, we can create a more secure digital ecosystem that fosters innovation, collaboration, and trust.
Conclusion
In today’s digital landscape, advanced encryption techniques play a vital role in safeguarding sensitive data and enabling secure communication. From symmetric algorithms like the Advanced Encryption Standard (AES) to asymmetric encryption schemes such as RSA and Elliptic Curve Cryptography (ECC), these powerful tools provide robust security measures for a wide range of applications. AES, in particular, stands out for its strong encryption capabilities, with key lengths of 128, 192, and 256 bits, and its resistance to practical cryptanalytic attacks to date.
As the field of quantum computing continues to advance, the future of encryption lies in the development and adoption of post-quantum encryption algorithms. These algorithms are designed to withstand the potential threats posed by quantum computers, ensuring the long-term security of encrypted data. Organizations and individuals must stay vigilant and proactive in implementing advanced encryption techniques, following best practices and utilizing well-tested libraries and tools to maintain the highest levels of data security.
In an increasingly connected world, the importance of advanced encryption cannot be overstated. From online banking and e-commerce to secure communication between applications, encryption plays a crucial role in protecting sensitive information and maintaining the trust of users. As concerns surrounding data privacy and security continue to grow, the continued development and widespread adoption of advanced encryption techniques will remain a top priority for businesses, governments, and individuals alike. By embracing the power of encryption, we can create a more secure digital future for everyone.