In today’s digital age, the internet has become an integral part of our daily lives. From online shopping and banking to social media and entertainment, we rely on the internet for countless activities. However, with the increasing number of internet-connected devices in the average US household, which reached around 25 in 2021 compared to just 11 in 2019, the importance of internet security and data protection cannot be overstated.
Cybersecurity threats are constantly evolving, and it’s crucial to stay informed about the best practices for secure browsing and online safety. Whether you’re using a computer, smartphone, tablet, or smart TV, taking proactive measures to protect your personal information and secure your devices is essential. By understanding the risks and implementing effective security measures, you can significantly reduce the chances of falling victim to cyber attacks, malware, and other online threats.
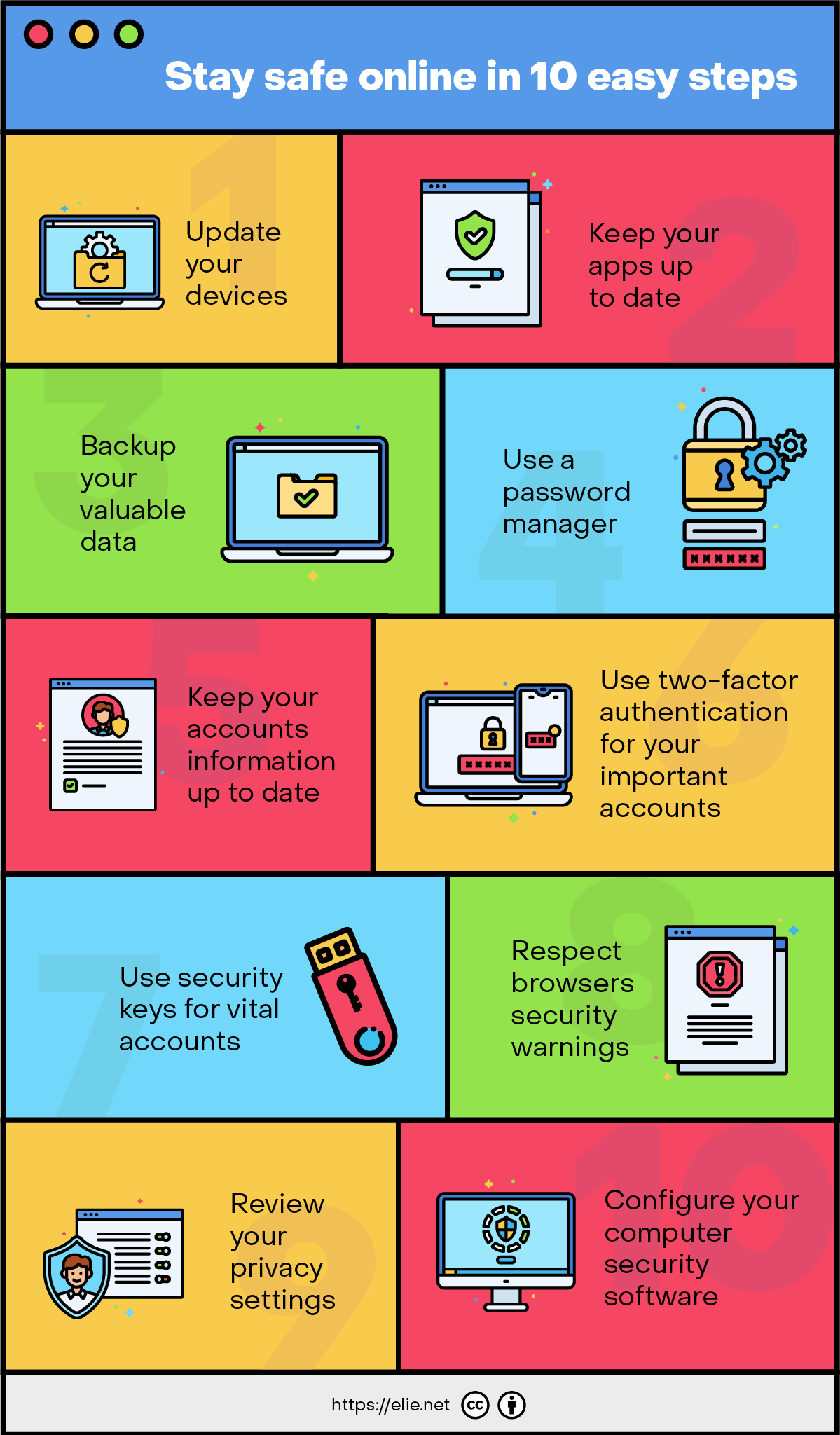
In this comprehensive guide, we’ll explore the key aspects of internet security and provide you with practical tips and strategies to help you stay safe online. From creating strong passwords and enabling multifactor authentication to recognizing phishing scams and keeping your software up-to-date, we’ll cover everything you need to know to enhance your cybersecurity and protect your digital life.
Key Takeaways:
- Use strong, unique passwords for each online account and enable multifactor authentication whenever possible.
- Regularly update your software and operating systems to patch security vulnerabilities.
- Be cautious when clicking links or downloading attachments from unknown sources.
- Secure all your devices, including smartphones, tablets, and smart TVs, with passwords or biometric authentication.
- Back up your important data regularly to protect against ransomware attacks and data loss.
- Use a reliable antivirus solution and scan your system for threats periodically.
- Stay informed about the latest cybersecurity trends and best practices to ensure your online safety.
Understanding the Importance of Internet Security
In today’s digital age, internet security has become a critical concern for individuals and businesses alike. As our lives increasingly revolve around online activities, from communication and entertainment to financial transactions and sensitive data storage, the need to protect ourselves from cyber threats has never been more pressing. With the rise of sophisticated malware, phishing scams, and data breaches, it is essential to understand the importance of internet security and take proactive measures to safeguard our digital lives.
The Growing Threat of Cyber Attacks
Cyber attacks have become a pervasive and costly problem worldwide. According to recent estimates, cybercrime is predicted to cost the world a staggering $10.5 trillion annually by 2025, with global cybercrime costs expected to increase by almost 15% yearly for the next four years. The cyber security market is also forecasted to grow significantly, from $217 billion in 2021 to $345 billion by 2026, reflecting the increasing demand for robust security solutions.
Cyber criminals employ various tactics to infiltrate systems and steal sensitive information. Malware, short for malicious software, is an umbrella term that encompasses a range of threats, including spyware, rootkit viruses, Trojan horses, and worms. These malicious programs can steal sensitive data, monitor user activity, interfere with network connections, and cause significant damage to computer systems. Phishing attacks, in which hackers disguise themselves as trusted sources to trick users into revealing personal information, are also on the rise, leading to an alarming increase in identity theft and financial fraud.
Protecting Your Personal Information Online
Safeguarding personal information is a critical aspect of internet security. However, many individuals remain unaware of the risks or fail to take adequate precautions. Studies have shown that a significant percentage of people do not bother with internet security, leaving themselves vulnerable to cyber attacks. The ratio of individuals using internet security software compared to those who do not is concerningly low, contributing to the high rate of internet fraud cases.
One of the most common vulnerabilities is weak or shared passwords. A staggering percentage of individuals admit to sharing their passwords with others, while many continue to use easily guessable or repetitive passwords across multiple accounts. This practice significantly increases the risk of successful phishing attempts and unauthorized access to sensitive information. To protect yourself, it is crucial to create strong, unique passwords for each account and consider using a reputable password manager for added security.
| Cyber Threat | Description | Impact |
|---|---|---|
| Malware | Malicious software designed to infiltrate and damage computer systems | Steals sensitive data, monitors user activity, and causes system damage |
| Phishing | Fraudulent attempts to obtain sensitive information by disguising as a trustworthy entity | Leads to identity theft, financial fraud, and unauthorized access to accounts |
| Weak Passwords | Easily guessable or repetitive passwords used across multiple accounts | Increases the risk of successful cyber attacks and data breaches |
By understanding the importance of internet security and adopting best practices, such as using strong passwords, keeping software up-to-date, and being cautious when clicking links or downloading attachments, individuals can significantly reduce their risk of falling victim to cyber attacks. As the digital landscape continues to evolve, prioritizing internet security is no longer an option but a necessity for protecting our personal information and maintaining a safe online presence.
Creating Strong and Unique Passwords
In today’s digital age, creating strong and unique passwords is essential for safeguarding your online accounts and personal information. Weak or easily guessable passwords can make you vulnerable to cyber attacks, identity theft, and unauthorized access to your sensitive data. By following best practices for password security and utilizing helpful tools like password managers, you can significantly enhance your online security and protect yourself from potential threats.
Characteristics of a Secure Password
A secure password should possess several key characteristics to ensure its effectiveness in protecting your online accounts. Here are some guidelines to follow when creating strong passwords:
- Length: Passwords should be at least 12 characters long, with 14 or more characters recommended for even greater security.
- Complexity: Include a combination of uppercase letters, lowercase letters, numbers, and symbols in your passwords.
- Uniqueness: Avoid using the same password for multiple accounts. Each account should have its own unique password to minimize the risk of a single breach compromising all your accounts.
- Avoid personal information: Refrain from using easily guessable information such as your name, birthday, username, email address, or family names in your passwords.
- Steer clear of patterns: Commonly used patterns like “ABC,” “12345,” or keyboard sequences are highly insecure and should be avoided.
A strong password example is “m#P52s@ap$V,” which contains over 10 characters and includes a mix of uppercase and lowercase letters, numbers, and symbols.
Using Password Managers for Added Security
Managing multiple unique and complex passwords can be challenging, which is where password managers come in handy. Password managers are software applications that securely store and manage your passwords, making it easier to maintain strong password security across all your accounts. Some popular password managers include:
| Password Manager | Key Features |
|---|---|
| LastPass | Cross-platform support, browser integration, password sharing |
| 1Password | Strong encryption, two-factor authentication, secure note storage |
| Dashlane | Automatic password changer, dark web monitoring, VPN integration |
| Google Chrome’s Password Manager | Built-in browser support, automatic password saving, password generation |
Using a password manager not only helps you generate and store strong, unique passwords but also enables you to easily update weak passwords and enable multi-factor authentication for an extra layer of security. By incorporating a password manager into your online security routine, you can significantly reduce the risk of password-related breaches and ensure the safety of your online accounts.
Remember, strong password security is an ongoing process. Regularly updating your passwords, using unique passwords for each account, and staying vigilant against phishing attempts are all crucial steps in maintaining a secure online presence. By prioritizing password security and adopting best practices, you can protect yourself and your valuable personal information from falling into the wrong hands.
Securing Your Internet Connection
In today’s digital age, ensuring the security of your internet connection is crucial for protecting your personal information and sensitive data. By implementing effective measures such as enabling firewalls, strengthening network security, and utilizing Virtual Private Networks (VPNs), you can significantly reduce the risk of falling victim to cyber threats and maintain a safe online experience.
Enabling Firewalls and Network Security
One of the first lines of defense in securing your internet connection is enabling firewall protection. A firewall acts as a barrier between your device and the internet, monitoring and filtering incoming and outgoing network traffic based on predetermined security rules. Most modern routers come equipped with built-in firewall capabilities, but it’s essential to ensure that this feature is activated in the router settings. By doing so, you add an extra layer of protection against potential hackers attempting to exploit vulnerabilities in your network.
In addition to enabling firewall protection, there are several other steps you can take to enhance your network security:
- Change the default router name (SSID) and password to prevent unauthorized access
- Use strong encryption methods such as WPA3 Personal or WPA2 Personal for your Wi-Fi network
- Keep your router software up to date to ensure you have the latest security patches and features
- Disable remote management and features like Wi-Fi Protected Setup (WPS) and Universal Plug and Play (UPnP)
- Set up a guest network with a separate name and password for visitors
- Always log out as an administrator after configuring your router settings
Using Virtual Private Networks (VPNs)
Another effective way to secure your internet connection is by using a Virtual Private Network (VPN). A VPN encrypts your internet traffic, making it unreadable to anyone who might intercept it, including your Internet Service Provider (ISP), hackers, and other malicious actors. When you connect to a VPN server, your online activities become anonymized, and your real IP address is masked, enhancing your privacy and security.
When choosing a VPN service, it’s crucial to opt for a reputable provider that offers robust encryption, a strict no-logging policy, and a wide network of servers. While free VPNs may be tempting, they often come with limitations and may compromise your security. Instead, consider investing in a trusted VPN service to ensure optimal protection. For example, NordVPN, a highly regarded VPN provider, offers its services on up to 6 devices simultaneously and operates an extensive network of 5,100 servers across 60 countries.
| VPN Provider | Key Features | Pricing |
|---|---|---|
| NordVPN | – Offers services on 6 devices – Operates 5,100 servers in 60 countries |
First year: $59.88 Regular price: $99.48 per year |
By implementing these security measures and best practices, you can significantly reduce the risk of falling victim to cyber threats and enjoy a safer, more secure online experience. Remember, investing in your internet security is a small price to pay for the peace of mind and protection it provides.
Recognizing and Avoiding Phishing Scams
In today’s digital age, phishing attacks have become a prevalent form of online fraud. Scammers launch thousands of these deceptive campaigns every day, using emails, text messages (known as smishing), and fake websites to trick individuals into revealing sensitive information or downloading malware. The consequences of falling victim to a phishing scam can be severe, including identity theft and financial loss.
To protect yourself from phishing attacks, it’s crucial to stay vigilant and learn to recognize the signs of a potential scam. Be wary of unsolicited emails or messages that create a sense of urgency, contain spelling and grammatical errors, or originate from unfamiliar senders. Legitimate companies will never request sensitive information like passwords or Social Security numbers via email or text.
According to the Federal Trade Commission, if you believe you’ve fallen victim to a phishing scam, it’s essential to take immediate action. Contact your financial institutions, place fraud alerts on your credit files, and report the incident to the proper authorities.
If you receive a suspicious email or encounter a questionable website, resist the temptation to click on any links or provide personal information. Instead, contact the company directly through a trusted channel to verify the authenticity of the communication. By taking a cautious approach and double-checking before engaging, you can significantly reduce your risk of falling prey to phishing scams.
To further safeguard your online presence, consider implementing the following measures:
- Enable multi-factor authentication on your accounts for an added layer of security
- Regularly update your software and operating systems to patch vulnerabilities
- Use a reputable antivirus solution and perform frequent scans for threats
- Back up your data to protect against potential loss in case of a successful phishing attack
By staying informed about the tactics used in phishing attacks and adopting smart online practices, you can significantly reduce your risk of becoming a victim of online fraud. Remember, if an offer seems too good to be true or a message appears suspicious, trust your instincts and err on the side of caution. Your vigilance is key to maintaining a safe and secure online experience.
Keeping Your Software and Operating System Up-to-Date
One of the most crucial aspects of maintaining a secure online presence is ensuring that your software and operating system are always up to date. Developers frequently release software updates, security updates, and firmware updates to address vulnerabilities, improve performance, and enhance user experience. By keeping your system current with the latest updates, you significantly reduce the risk of falling victim to cyber threats.
The Importance of Regular Updates and Patches
Threat actors are constantly on the lookout for vulnerabilities in operating systems and applications. If you fail to install updates regularly, you expose your system to potential exploits. According to recent studies, outdated software can create vulnerabilities, allowing cyber criminals to access sensitive information. In fact, malware such as viruses and trojans often exploit system vulnerabilities to gain unauthorized access.
To combat these threats, developers of operating systems and applications frequently release patches for vulnerabilities. These updates not only fix security issues but also improve performance, compatibility, and introduce new features. By keeping your software up to date, you significantly reduce your system’s vulnerability and lower the risk of falling victim to cyber-attacks.
| Software | Update Frequency | Update Method |
|---|---|---|
| Windows OS | Monthly | Automatic updates through system settings |
| macOS | Periodic | Manual or automatic updates via App Store |
| iOS | Periodic | Manual or automatic updates through settings |
| Android | Varies by device | Manual updates through device settings |
Enabling Automatic Updates for Convenience
To ensure that your system remains protected against the latest threats, it is highly recommended to enable automatic updates. This proactive measure ensures that your software and operating system are always up to date without requiring manual intervention. Most modern operating systems, including Windows, macOS, iOS, and Android, offer automatic update features.
For example, the University of Idaho’s Administrative Procedures Manual (APM) 30.111 mandates that all university-owned devices must be configured to automatically receive and install software updates. Additionally, the OIT Data Security Standards require that all devices connected to the university network must have the latest security patches installed within 30 days of their release. Devices that fail to comply with these standards may be blocked from accessing the network until they are updated.
“Regularly updating software is one of the easiest ways to protect against cyber-threats. Failure to keep computers updated makes systems more vulnerable to cyber-attacks.”
In conclusion, keeping your software and operating system up to date is a critical component of maintaining a secure online presence. By regularly installing updates and enabling automatic updates, you can significantly reduce your system’s vulnerability to cyber threats, improve performance, and take advantage of the latest features. Stay vigilant, stay updated, and stay safe online.
Internet Security Best Practices
In today’s digital age, practicing safe browsing habits and being vigilant about internet security is more important than ever. By adopting a few key best practices, you can significantly reduce your risk of falling victim to cyber threats and protect your sensitive information online.
Being Cautious When Clicking Links and Downloading Attachments
One of the most critical aspects of maintaining internet security is exercising caution when clicking links or downloading attachments, especially from unknown sources. Cybercriminals often use suspicious downloads and malicious links to distribute malware, such as viruses, Trojan horses, and spyware. To minimize these risks:
- Avoid downloading unlicensed software, pirated programs, or files from untrustworthy websites.
- Be wary of email attachments from unknown senders, as they may contain malware like macro viruses or ransomware.
- Hover over links before clicking to ensure they lead to legitimate websites.
- Keep your antivirus and anti-malware software up-to-date to detect and prevent potential threats.
Avoiding Unsecured Public Wi-Fi Networks
While public Wi-Fi networks at parks, malls, or airports offer convenience, they also pose significant security risks. These networks are often unsecured, making it easier for cybercriminals to intercept your data or initiate Man-in-the-Middle (MitM) attacks. To protect yourself when using public Wi-Fi:
- Avoid accessing sensitive information, such as online banking or personal emails, on public networks.
- Use a Virtual Private Network (VPN) to encrypt your internet connection and safeguard your data.
- Disable automatic Wi-Fi connections on your devices to prevent inadvertently connecting to unsecured networks.
- Be cautious of fake public Wi-Fi networks set up by threat actors to steal your information.
Regularly Backing Up Your Data
Even with robust cybersecurity measures in place, data loss can still occur due to hardware failure, virus infections, or other unforeseen events. To minimize the impact of such incidents, it’s crucial to regularly back up your important files and data. Consider the following backup strategies:
- Store your original data on your computer and periodically back it up to an external hard drive.
- Sign up for a reputable cloud backup service that automatically saves your data offsite.
- Implement a 3-2-1 backup strategy: Keep at least three copies of your data, store them on two different media types, and maintain one copy offsite.
| Backup Strategy | Advantages |
|---|---|
| External Hard Drive | Provides a local backup solution, allowing for quick data restoration. |
| Cloud Backup Service | Offers remote data storage, protecting against local disasters and enabling access from anywhere with an internet connection. |
| 3-2-1 Backup Strategy | Ensures multiple copies of your data are available, minimizing the risk of complete data loss. |
“The only way to be truly secure is to understand the threats you face and take proactive measures to minimize your risk exposure.”
By adopting these internet security best practices, you can significantly enhance your online safety and protect your valuable data from falling into the wrong hands. Remember, staying vigilant and informed is key to navigating the digital landscape securely.
Enhancing Browser Security
Your web browser is your gateway to the internet, so ensuring its security is crucial for protecting your online activities. By choosing a secure web browser and installing browser extensions, you can significantly enhance your browsing experience and safeguard your personal information.
Choosing a Secure Web Browser
When selecting a web browser, consider its built-in security features and reputation for protecting user privacy. Some popular browsers, such as Google Chrome and Microsoft Edge, offer advanced security settings that can help defend against online threats.
| Browser | Security Features |
|---|---|
| Microsoft Edge |
|
| Google Chrome |
|
When browsing the web, always look for the website security padlock icon in the address bar. A secure URL begins with “HTTPS” rather than “HTTP,” indicating that the website has a secure sockets layer (SSL) in place. However, keep in mind that the presence of the padlock and HTTPS doesn’t guarantee the website’s legitimacy, so be cautious when engaging with unfamiliar sites.
Installing Browser Extensions for Added Protection
In addition to the built-in security features of your web browser, consider installing trusted browser extensions to further enhance your online security. These extensions can help block unsafe content, such as scams and malware, and provide an extra layer of protection while browsing.
Malwarebytes Browser Guard is a browser extension for Chrome, Safari, and other browsers that secures your internet experience by blocking unsafe content like scams and malware.
To maximize your browser security, utilize your antivirus solution to protect your system from malicious software targeting your network or web browser. While operating systems often include built-in antivirus software, it may not protect popular third-party browsers like Google Chrome by default. Consider downloading anti-malware software that specifically shields your browser and defends against new and emerging threats, as legacy antivirus tools may not be as effective against unknown risks.
By selecting a secure web browser, being vigilant about website security indicators, and installing trusted browser extensions, you can significantly enhance your online security and enjoy a safer browsing experience.
Protecting Your Children Online
In today’s digital age, online safety for kids is a top priority for parents. Children’s innocence, curiosity, and desire for independence make them particularly vulnerable to internet dangers such as cyberbullying and online predators. To ensure your children’s safety, it is crucial to implement parental controls and establish open communication about their online activities.
Cyberbullying has become a significant concern, especially as children gain access to various online platforms like email, instant messaging, chat rooms, and social networking sites. Educating your children about the risks of sharing personal information and encountering cyberbullies is essential to increase their awareness without causing undue fear.
Online predators pose a serious threat to children due to the anonymity the internet provides, making it easier for them to misrepresent themselves and manipulate young users. Parents should be vigilant in monitoring their children’s online interactions and the websites they visit to prevent potential exploitation.
To effectively protect your children online, consider the following measures:
- Keep the computer in an open area to easily monitor your children’s online activities
- Set clear rules and boundaries for computer use based on your child’s age, knowledge, and maturity, including time limits, approved websites, and permissible activities
- Utilize parental controls in web browsers or specialized software programs to regulate and monitor your children’s online behavior
- Implement separate user accounts on the computer to restrict access and prevent unintentional file modifications or deletions
- Maintain open communication with your children, encouraging them to discuss any concerns or issues they encounter online
| Parental Control Type | Description |
|---|---|
| Network-level controls | These controls are applied at the router level, affecting all devices connected to the home network |
| Device-level controls | These controls are specific to individual devices, such as smartphones, tablets, or computers |
| Application controls | These controls target specific applications or software programs, limiting access or functionality |
“The iGuardian Program, Stay Safe Online Campaign, Stop. Think. Connect. Toolkit, and Concerned Parent’s Internet Safety Toolbox are excellent resources for parents seeking to protect their children online.”
By staying informed, setting boundaries, and maintaining open communication, parents can significantly reduce the risks their children face in the digital world. Remember, your involvement and guidance are essential in ensuring your children’s online safety and helping them navigate the internet responsibly.
The Role of Antivirus and Anti-Malware Software
In today’s digital landscape, antivirus software and anti-malware solutions play a crucial role in maintaining online security. These programs are designed to detect, prevent, and eliminate various cyber threats, including viruses, malware, spyware, and ransomware. By employing a combination of reactive file scanning, real-time protection, and comprehensive system scans, antivirus software provides an essential layer of defense against the ever-evolving world of cyber threats.
Choosing a Reliable Antivirus Solution
With numerous antivirus software options available in the market, selecting a reliable solution is paramount to ensure effective protection. Industry-leading providers such as McAfee, Norton, Webroot, and Bitdefender offer robust security features and frequent updates to combat the latest threats. When choosing an antivirus program, consider factors such as detection rates, performance impact, user-friendliness, and additional features like VPNs, identity theft protection, and parental controls.
| Antivirus Software | Key Features |
|---|---|
| McAfee | Real-time scanning, web protection, VPN, identity monitoring |
| Norton | Malware detection, firewall, password manager, cloud backup |
| Webroot | Cloud-based scanning, fast installation, minimal system impact |
| Bitdefender | Advanced threat detection, ransomware protection, VPN, parental controls |
Regularly Scanning Your System for Threats
To maintain optimal protection, it is essential to perform regular system scans using your antivirus software. These scans can identify and remove any dormant or hidden threats that may have infiltrated your system. Most antivirus programs offer both quick scans for immediate threats and full system scans for more comprehensive coverage. Scheduling automatic scans and keeping your antivirus software up-to-date ensures that your system remains protected against the latest cyber threats.
Industry statistics indicate that utilizing a layered security approach, combining antivirus and anti-malware software, is highly recommended by security experts for comprehensive protection against a wide range of cyber threats.
While no antivirus software is 100% accurate, choosing a reliable solution and maintaining regular scans significantly reduces the risk of falling victim to malicious attacks. By investing in robust antivirus protection and staying vigilant online, you can safeguard your personal information, financial data, and overall digital well-being.
Conclusion
In today’s digital age, internet security is more critical than ever. With the increasing frequency and sophistication of cyber attacks, it is essential for individuals to take proactive measures to protect their personal information and online presence. By implementing strong and unique passwords, securing internet connections, recognizing and avoiding phishing scams, keeping software and operating systems up-to-date, and following best practices, users can significantly reduce their risk of falling victim to cybercrime.
Remember, 63% of internet users admit to using the same password across multiple accounts, and 91% of successful data breaches begin with a phishing email. These statistics highlight the importance of being vigilant and taking internet security seriously. By educating yourself and staying informed about the latest threats and best practices, you can enjoy the benefits of the internet while minimizing the risks.
In addition to individual responsibility, it is crucial for organizations and service providers to prioritize cybersecurity. This includes implementing robust security measures, regularly updating software and systems, conducting security audits, and being transparent with users about their data practices. By working together and remaining proactive, we can create a safer and more secure online environment for everyone.
One comment